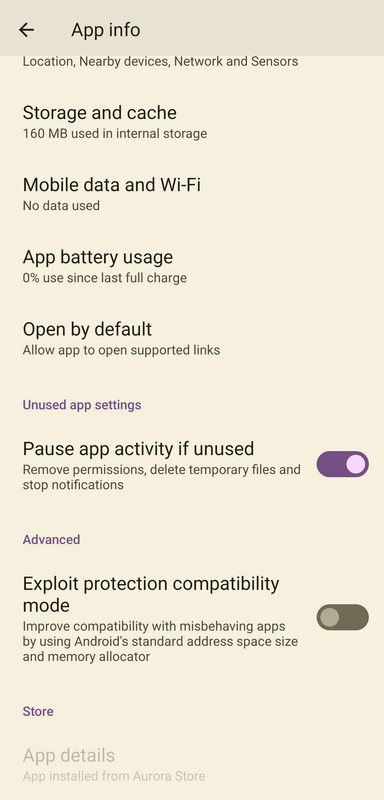
I was reading through the Usage guide where it describes this menu under the Bugs uncovered by security features section. I have a misbehaving app for which I would like to narrow down the cause. The guide indicates that there are separate toggles for the memory allocator and the address space size in this menu, but nothing comes up by searching.
Where would I find the "configure hardening menu"?
I think what you look for is the exploit protection compatibility mode. You find this under your apps settings when you go in the menu of an APP where you can set restrictions etc.
Theres a toggle for this.
MineralWater Indeed, I have seen this toggle. But the Usage guide is clear that there are also separate toggles for each of the memory allocator and address space, not only a single toggle.
- Edited
Harald what you're looking for is under:
Settings > Apps > AppName > Configure hardening
It's just above the Exploit protection compatibility mode toggle.
mythodical I must be blind because I still do not see a "configure hardening" option. Would you kindly circle it in my screenshot?
I used to have the configure hardening option, but now it's not showing up on my phone too. I only ever use exploit compatibility mode, so I hadn't noticed. Not sure how long it's been gone.
- Edited
Harald that's odd because my Pixel 7 has the menu option. Running version TQ1A.221205.011.2022121400.
Edit: here is a screenshot of the sub-menu.
mythodical I have the same build number on a P7Pro. I doubt that Pro vs not-Pro is the reason you have it while I do not. What else could it be?
[deleted]
unwat I've just checked and I have it the same as you. Being on P6a I had these options but they are missing now. I tried to search it in settings, just to be sure, that the options isn't moved elsewhere, but I found nothing.
Harald my guess is that it's only available for certain apps. I see that some apps don't even list the exploit protection compatibility toggle. For example, the default Messaging app, Simple File Manager, and DAVx⁵ all lack the compatibility toggle and hardening menu.
I checked Material Files, same version as the one you have in your screenshot, and I still don't have that option. Checked both owner and my regular profile just in case. Pixel 6 here.
If I were to guess, this changed in the 2022120600 release. Looks like there were many changes to how they determine whether these options can be set for an app. I'm not an Android dev so I'm slow to work everything out and I've run out of time to read the code they have.
There's a GrapheneOS package state that's added to the Android package manager. Settings checks a package's state and if the package has a flag ENABLE_COMPAT_VA_39_BIT, then that extra menu is displayed in settings. Couldn't figure out when it's showed and under what circumstances...
What threat model would require the user to simply avoid the app instead of using the toggle?
Also miss this on p6p
The toggles are for compatibility. You don't want to use those toggles. Toggling either of them on is reducing your phone's security rather than increasing it.
ENABLE_COMPAT_VA_39_BIT switches back to Android's default 39-bit address space:
4-level page tables are enabled on arm64 to provide a much larger address space (48-bit instead of 39-bit) with significantly higher entropy Address Space Layout Randomization (33-bit instead of 24-bit).
DISABLE_HARDENED_MALLOC turns this off:
Our own hardened malloc (memory allocator) leveraging modern hardware capabilities to provide substantial defenses against the most common classes of vulnerabilities (heap memory corruption) along with reducing the lifetime of sensitive data in memory.
Both quotes come from the website here.
A better question would be if disabling these features is necessary to run an app, is it better to just not use the app entirely?
Hardened malloc can protect against severe vulnerabilities (including 0-days), so if you want to protect yourself from memory bugs, don't use apps that require you to disable hardened_malloc. Memory bugs are the main reason Google is migrating to Rust in its code base moving forward. Same for the Linux kernel.
I'm not familiar with the address space one, but it appears it helps make exploiting memory bugs much more difficult. https://en.wikipedia.org/wiki/Address_space_layout_randomization