In Android, the IP-based data layer is end-to-end encrypted, but the same is not true for voice and SMS traffic on telephone networks. Its encryption remains under the control of the operator, without any type of control by the user, who cannot know if the data is encrypted or not.
This enables another possible attack, when a device like StingRay makes the mobile believe that the network does not support encryption, so that it switches to an unencrypted connection, thus potentially being intercepted.
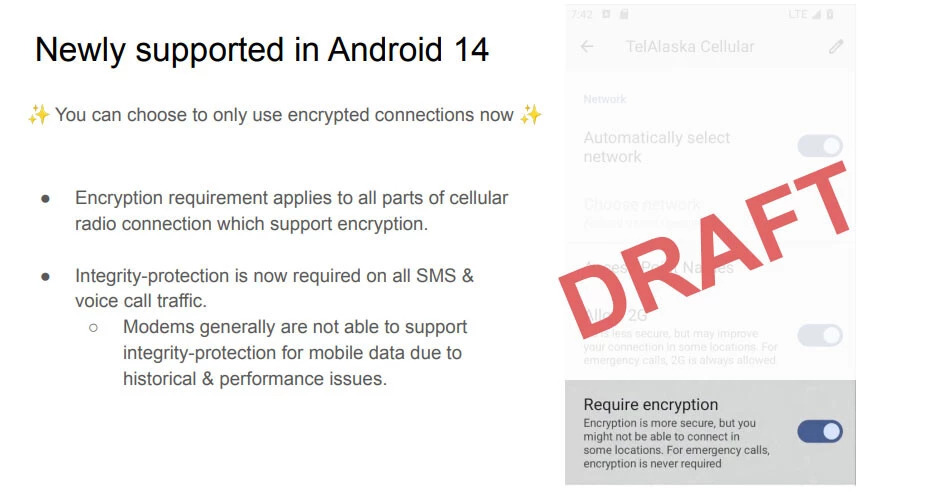
I have not found this option either in Android 14 G stock or in graphene.